In this procedure we create a network file share by integrating the open source program Samba running on Linux with Active Directory to authenticate access to the network file share.
Business case
A computer running Linux and Samba can create a network file share authenticating against a company’s Active Directory. This means that a Linux server and Samba network file share software can replace a Windows server for the network file share role in the enterprise, reducing software licensing costs and improving security and stability.
This procedure was tested on Ubuntu Linux 22.04 LTS
This procedure was tested on Ubuntu Linux 22.04 LTS
Understanding the test network
This procedure was tested on a network of 3 virtual machines, each running in bridge mode, on different hypervisor hosts.
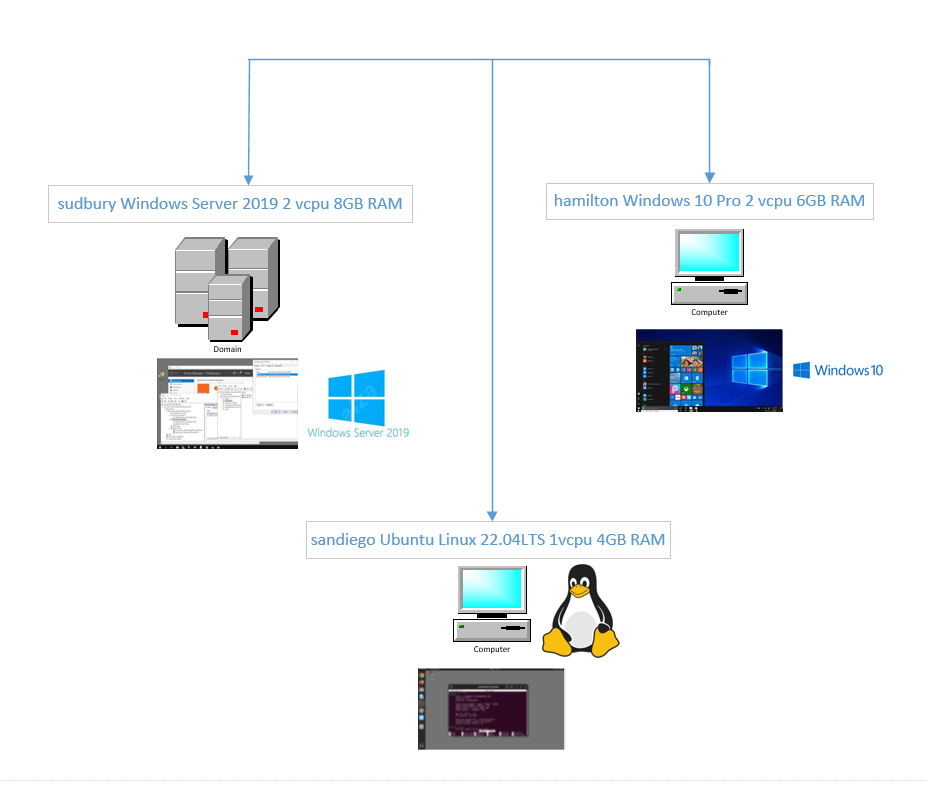
| sudbury | Windows Server 2019 acting as Active Directory controller for the clarkcounty.gordonbuchan.com domain. |
| sandiego | Ubuntu Linux 22.04LTS desktop joined to the clarkcounty.gordonbuchan.com domain, authenticating access to a network file share enabled by Samba and Winbind against the Active Directory controller for the domain clarkcounty.gordonbuchan.com on sudbury. |
| hamilton | Windows 10 Pro workstation joined to the clarkcounty.gordonbuchan.com domain. |
Understanding Active Directory
Active Directory is commercial software developed by Microsoft that runs primarily on Windows Server. Active Directory can authenticate users and groups of users, and can control access to resources like network file shares and “Single Sign-On” (SSO) login to computers connected to the network.
Understanding Samba
Samba is open source free software that enables a Linux server to provide a network file share that can be accessed by Windows computers.
A note re Samba’s included Active Directory functionality
Samba itself is able to act as an Active Directory controller and can implement a subset of Active Directory’s features. This post assumes that you are authenticating against an Active Directory controller running on Windows Server.
Understanding Winbind
Winbind is software that enables Samba to integrate with Active Directory to authenticate access to a network file share.
Understanding System Security Services Daemon (SSSD)
SSSD is a technology that enables Active Directory integration for Linux workstations. In practice, it is difficult to integrate SSSD with Samba for Active Directory authentication in a stable fashion. There are some approaches to SSSD which incorporate Winbind for a hybrid approach. This procedure will focus on using Winbind, and without using SSSD.
Choosing Winbind over SSSD for a network file share authenticaticated against Active Directory
This procedure will use Winbind to enable Samba to integrate with Active Directory to create a network file share authenticated against Active Directory.
Objectives
- Access to the network file share authenticated against Active Directory.
- The network file share must be accessible to workstations with “Enable insecure guest logins” set to “Disabled.”
- The network file share must observe ACL and allow overrides by Windows clients for ownership and permissions.
(Single-Sign-On (SSO) and SSSD will be addressed in a later procedure.)
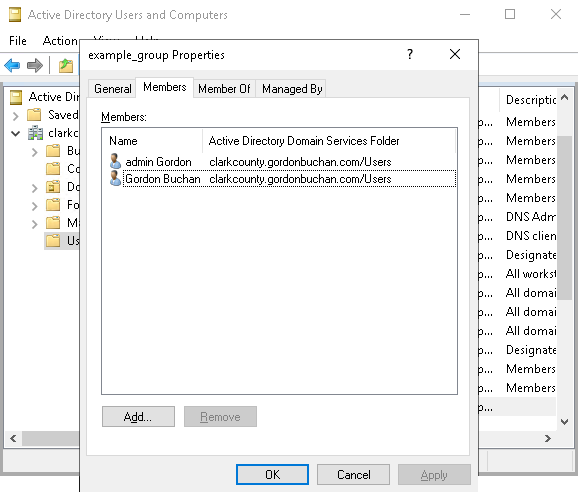
Creating the Active Directory group example_group and adding members to the group
Entering commands as root
This procedure assumes that you are logged in as the root user of the Linux server.
Escalate to the root user:
sudo su
Replacing the example realm/domain name with your realm/domain name
Please replace the sample realm/domain name clarkcounty.gordonbuchan.com with your realm/domain name.
Setting the system hostname
hostnamectl set-hostname sandiego.clarkcounty.gordonbuchan.com
Configuring the /etc/hosts file
Associate the host name of your Linux server with its IP address:
cd /etc
nano hosts
192.168.33.110 sandiego
192.168.33.110 sandiego.clarkcounty.gordonbuchan.com
Setting DNS
Disable systemd-resolved service:
systemctl stop systemd-resolved
systemctl disable systemd-resolved
Unlink the symbolic link /etc/resolv.conf:
cd /etc
unlink resolv.conf
Creating a new /etc/resolv.conf file
Ensure that the first nameserver entry is the IP address of the Active Directory server.
nano resolv.conf
nameserver 192.168.33.80
nameserver 8.8.8.8
search clarkcounty.gordonbuchan.com
reboot
Installing software
apt install acl samba winbind libnss-winbind krb5-user
Note: for the files /etc/krb5.conf and /etc/samba/smb.conf, the realm/domain name must be in UPPERCASE letters
The realm/domain name must be in UPPERCASE letters. This includes the long version CLARKCOUNTY.GORDONBUCHAN.COM and short version CLARKCOUNTY of the realm/domain name.
Configuring Kerberos
cd /etc
cp krb5.conf krb5.conf.orig
nano krb5.conf
[libdefaults]
default_realm = CLARKCOUNTY.GORDONBUCHAN.COM
dns_lookup_realm = false
dns_lookup_kdc = true
Configuring Nsswitch
cd /etc
cp nsswitch.conf nsswitch.conf.orig
nano nsswitch.conf
passwd: files winbind
group: files winbind
hosts: files dns wins
chmod 550 nsswitch.conf
Configuring Samba (1/2)
cd /etc/samba
cp smb.conf smb.conf.orig
nano smb.conf
[global]
realm = CLARKCOUNTY.GORDONBUCHAN.COM
security = ADS
workgroup = CLARKCOUNTY
idmap config SAMDOM : range = 10000 - 999999
idmap config SAMDOM : backend = rid
idmap config * : range = 3000-7999
idmap config * : backend = tdb
map acl inherit = Yes
vfs objects = acl_xattr
dedicated keytab file = /etc/krb5.keytab
kerberos method = secrets and keytab
winbind refresh tickets = Yes
Obtaining a Kerberos ticket
kinit admingordon
klist
Joining the Active Directory domain
net ads info testjoin
net ads -v join -U admingordon
net ads info
Restarting services (1/2)
systemctl restart smbd nmbd winbind
Creating the share folder
cd /home
mkdir example_share
chmod -R 2770 example_share
chown -R "CLARKCOUNTY\admingordon":"CLARKCOUNTY\example_group" example_share
Configuring Samba (2/2)
cd /etc/samba
cp smb.conf smb.conf.orig
nano smb.conf
[Share]
acl_xattr:ignore system acl = Yes
acl allow execute always = Yes
acl group control = Yes
inherit acls = Yes
inherit owner = windows and unix
inherit permissions = Yes
path = /media/share
read only = No
Restarting services (2/2)
systemctl restart smbd nmbd winbind
Mapping sid==5-1-5-32-546 to nogroup
This SID must be mapped to the UNIX group nogroup:
net groupmap add sid=S-1-5-32-546 unixgroup=nogroup type=builtin
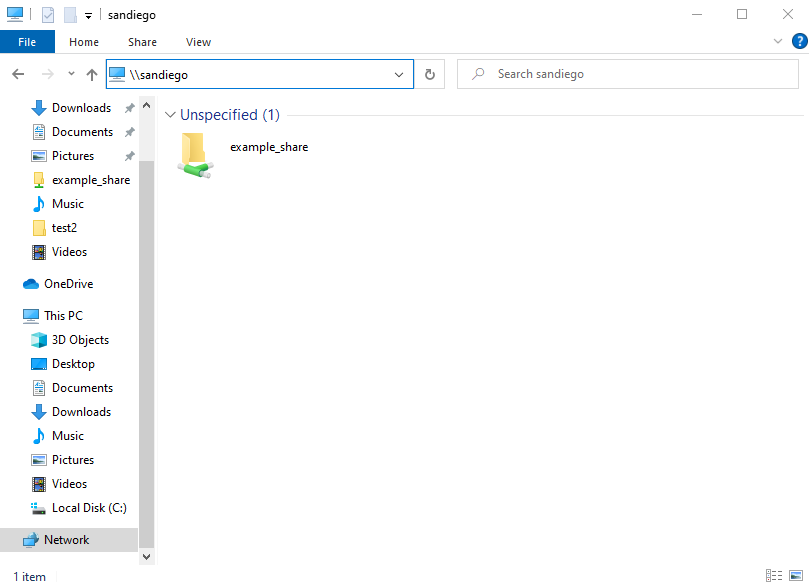
Connecting to the network file share from a Windows computer joined to the domain
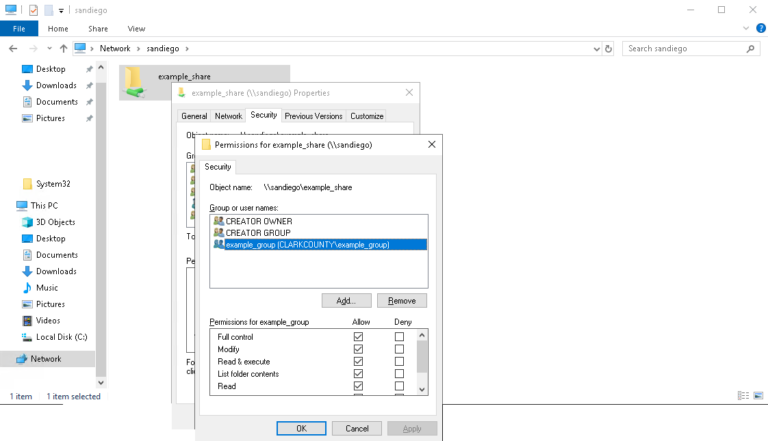
Applying Windows Access Control Lists (ACLs) from a Windows computer joined to the domain
References
http://blog.jrg.com.br/2021/02/01/ubuntu-focal-fossa-samba-domain-member-shares-1/
https://docs.vmware.com/en/VMware-Horizon-7/7.13/linux-desktops-setup/GUID-F8F0CFCF-C4D6-4784-85FF-E7C6DF575F49.html
https://ubuntu.com/server/docs/service-sssd-ad
https://wiki.samba.org/index.php/Setting_up_Samba_as_a_Domain_Member
https://www.jurisic.org/post/2021/11/24/SAMBA-Domain-Member-as-File-Server
https://www.moderndeployment.com/windows-server-2019-active-directory-installation-beginners-guide/
https://www.reddit.com/r/Ubuntu/comments/h01i2w/cheat_sheet_on_how_to_configure_a_smb_file_server/
